Pew Pew - sniper bots on Github to deliver RedLine Stealer
Last updated: Mar 6, 2023
Today, I came across an executable called uniswap-sniperbot-setup.exe that cought my attention. I had no idea what Uniswap and what a sniper bot is.
If you are as curious as me: Uniswap is a crypto, web3, NFT, whatever protocol. And a sniper bot is a program that automates ‘sniping’, or placing a last-second bid on an auction item.
Running the executable in a sandbox revealed that it bundles RedLine Stealer malware. The detected malware family is quite old. However, the observed delivery method is remarkable. The effort that went into the quality of the Github profile and repository page is impressive and will be illustrated below.
Malware Family
A detailed analysis of the behavior, which I can confirm, has been provided by SecurityScorecard.
TLDR:
RedLine is a stealer distributed as cracked games, applications, and services. The malware steals information from web browsers, cryptocurrency wallets, and applications such as FileZilla, Discord, Steam, Telegram, and VPN clients. […] The stealer implements the following actions that extend its functionality: Download, RunPE, DownloadAndEx, OpenLink, and Cmd.
Hashes and C2 server (82.115.223.177) have zero detections on VT at this point in time, so the current sample seems to be pretty new.
Delivery via Github
The executable originates from a password-protected .zip file hosted on Github. It pretends to be a useful tool that helps you to get rich with cryptocurrencies. Reports show that Github has been used in the past to deliver RedLine Stealer already (ORKL.eu), but often these Malicious Github profiles were easy to spot. Not so in this case.
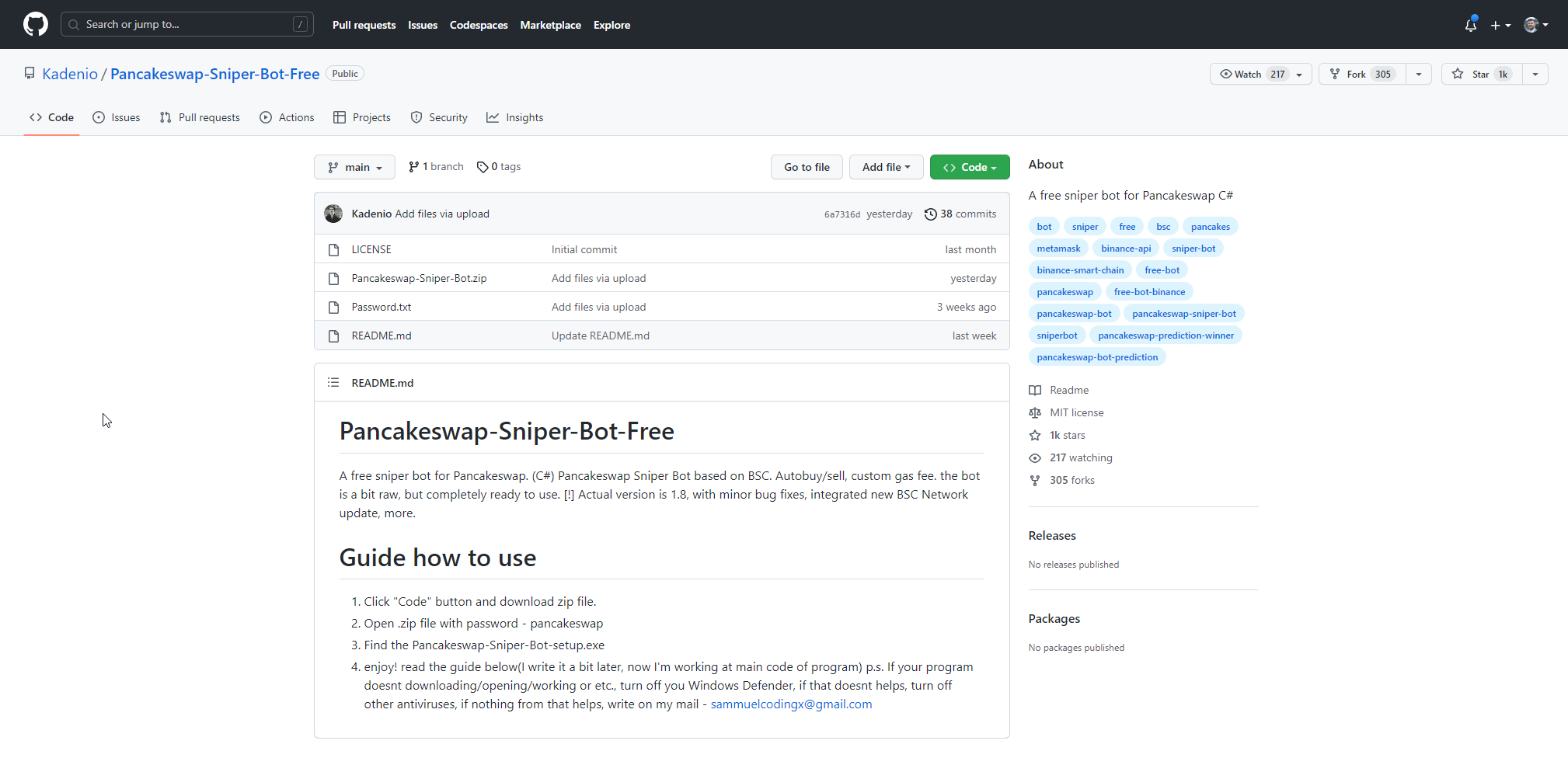
Repository
At first glance, the Uniswap-Sniper-Bot-Free repo has a nicely written README, an MIT license file, and a community with over 300 stars and nearly 200 forks.
However, the stars/forks ratio looks unusual. Seems like a lot of forks compared to the number of stars - more on that later.
Profile
Looking into the author’s profile (Kadenio), it has a sympathic introduction, a funny profile picture, status and location configured.
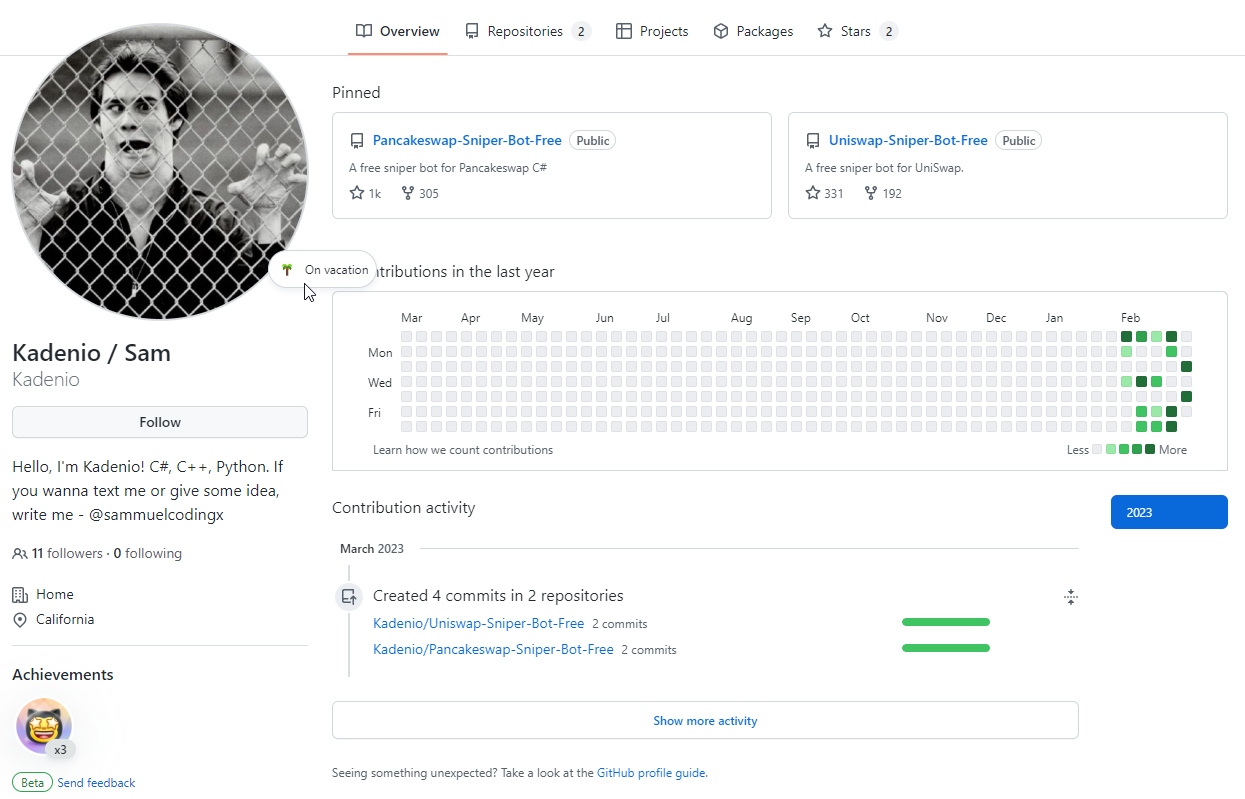
Besides the Uniswap-Sniper-Bot-Free repo, there is also a Pancakeswap-Sniper-Bot-Free repo on that profile. It is even more popular and has over 1000 stars and more than 305 forks.
Overall, the efforts to make the Github presence look harmless work quite well. Unlike the empty, short-lived profiles that were often used to spread malware in the past, this profile cannot be identified as malicious so easily.
Uncovering Github sniper bot network
If this was a normal Github profile, we would be done here. But as we have seen, the profile is hosting malware, how could it get so many stars and forks?
Time to look at that in a structured way. Using Python and the Github API, I recursively followed all forks and their corresponding owners for all repositories having sniper in their name. The resulting graph can be found in the following picture.
Apart from two exceptions, the owners of the forks do only have sniper bot repositories. They are only created to have forks of the source Kadenio account. When there are accounts with additional repositories, most of the time they contain malware, too.
Besides the forks, we can also retrieve all profiles that starred a given repo using Github’s stargazers API. Unsurprisingly, there is a large overlap here with profiles that have also forked the Kadenio repos. But as there are a lot more stars than forks, there must be additional profiles. And here’s how they look like. Completely empty, no content, just created to leave one star for the malicious source repo:
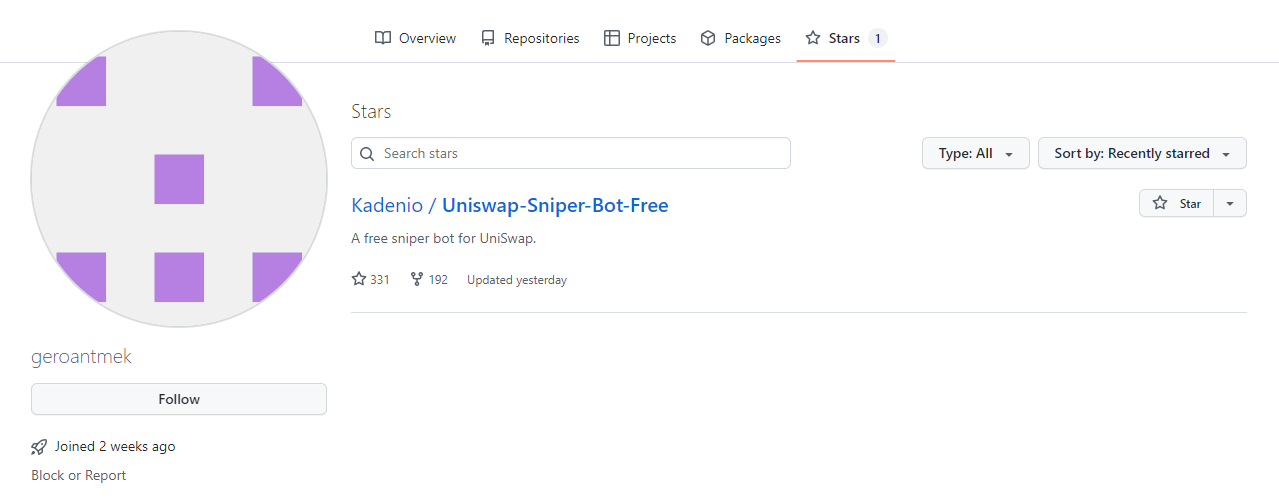
The whole network is created to fake a community to add credibility for the central Kadenio profile.
Summary
Well-crafted Github profiles, long-term account activity, and an active community are not a measure of trustworthiness. Always be vigilant with software from Github, even if the typical criteria look nice.
Samples
The original source can be found here, but it has been reported, so may be taken offline soon.
Fortunately, the author added MIT license, so I am allowed to redistribute both repositories to you 😉. Password infected. The samples change with each commit, so by checking out the git history, we can follow the malware development over time:
Uniswap-Pancakeswap-sniper-bot.zip
IOCs
- Executable: a392717edb6130e251f0765325f47db5f290a80cbbd57992af9ff62f4a6e7ae5
- C2 Server: 82.115.223.177
- Username: Kadenio
- Repo URL: hxxps://github.com/Kadenio/Uniswap-Sniper-Bot-Free
- Repo URL: hxxps://github.com/Kadenio/Pancakeswap-Sniper-Bot-Free
- Committer: 123904382+Kadenio[@]users.noreply.github.com

